JS逆向之百度翻译
前言
本文使用JS逆向的方法破解百度翻译;本文章仅用于笔者记录学习过程,请遵守相关法律法规,严禁用于非法途径。若读者因此作出任何危害网络安全的行为,后果自负,与笔者无关。
分析数据来源
- 打开百度翻译网站,在输入框输入需要翻译的单词:例如spider,右键查看网页源代码,在网页源代码中搜索spider,发现并没有spider单词,因此可以判断请求百度翻译翻译单词的过程应该是一个异步请求;
获取需要请求的数据
根据上文的判断这应当是一个异步请求;按下F12然后刷新网站页面,获取加载网站的JS,CSS等文件;
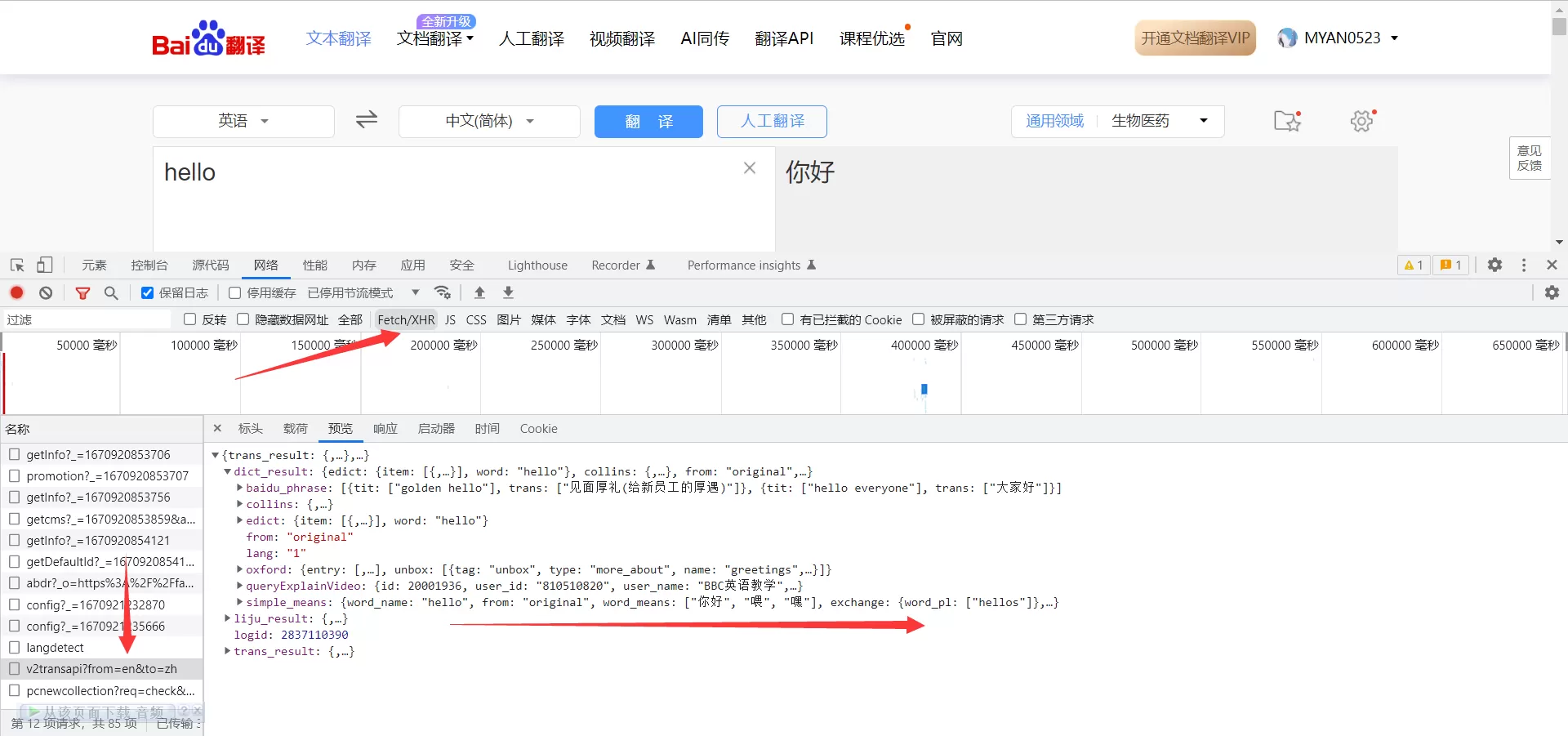
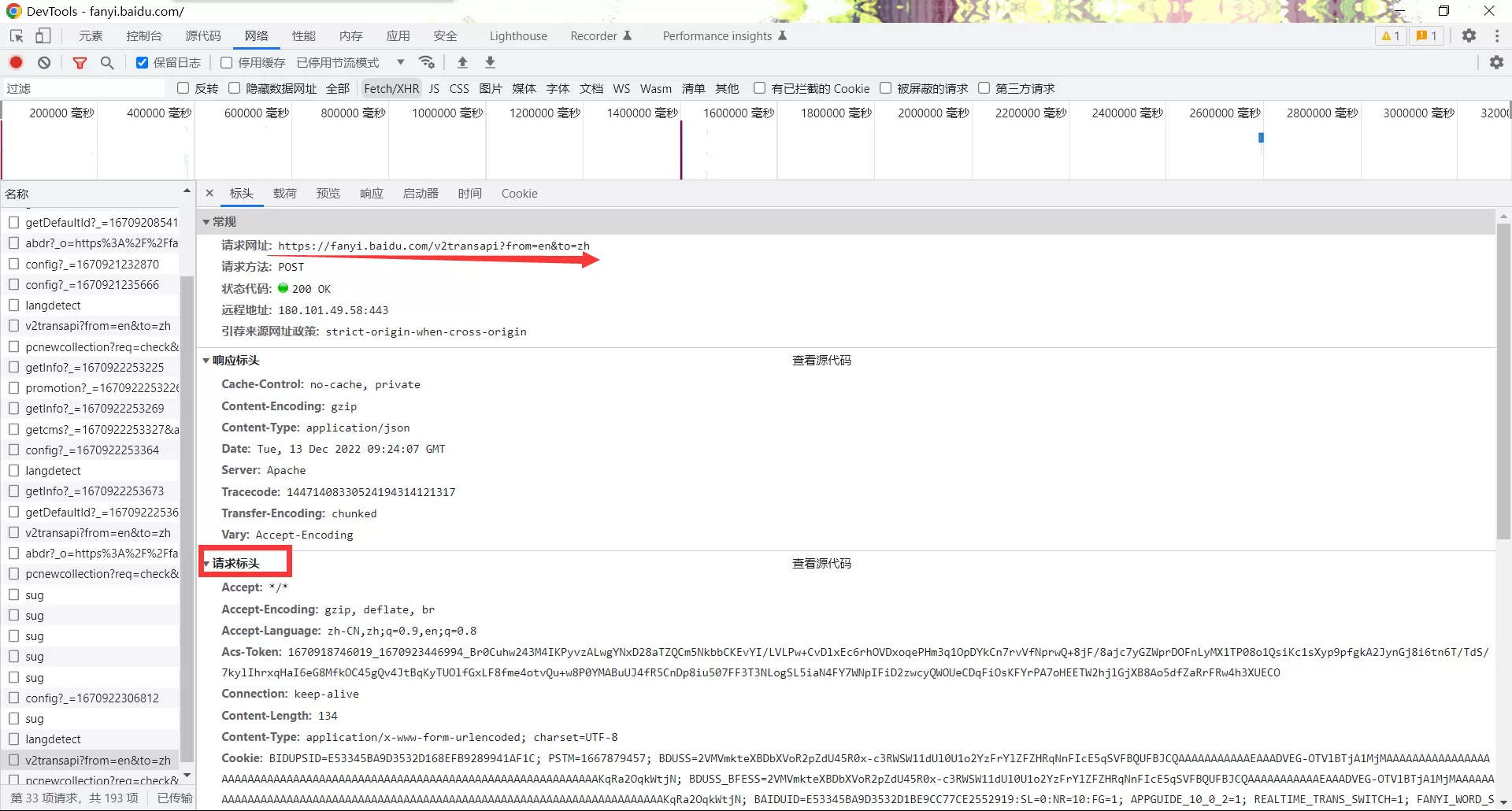
在输入框中输入查询单词,例如hello;查看发送的异步请求,一个一个查看,观察哪一个请求的响应是获得翻译结果的;这里判断应当是v2开头的这个请求;
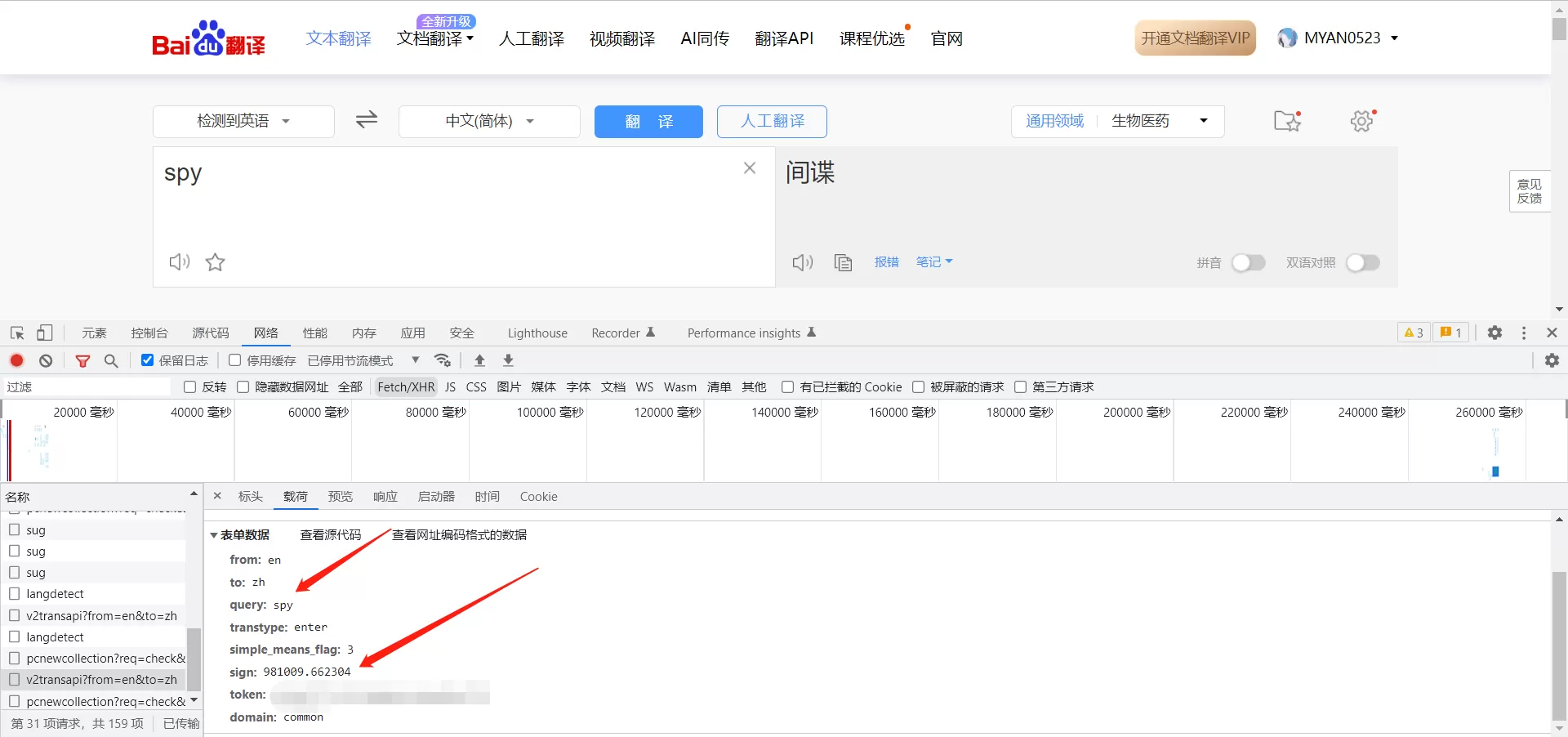
查看请求头,发现这是一个post请求,根据表单数据初步判断可能有两项请求内容是变化的,一个是sign一个是token;
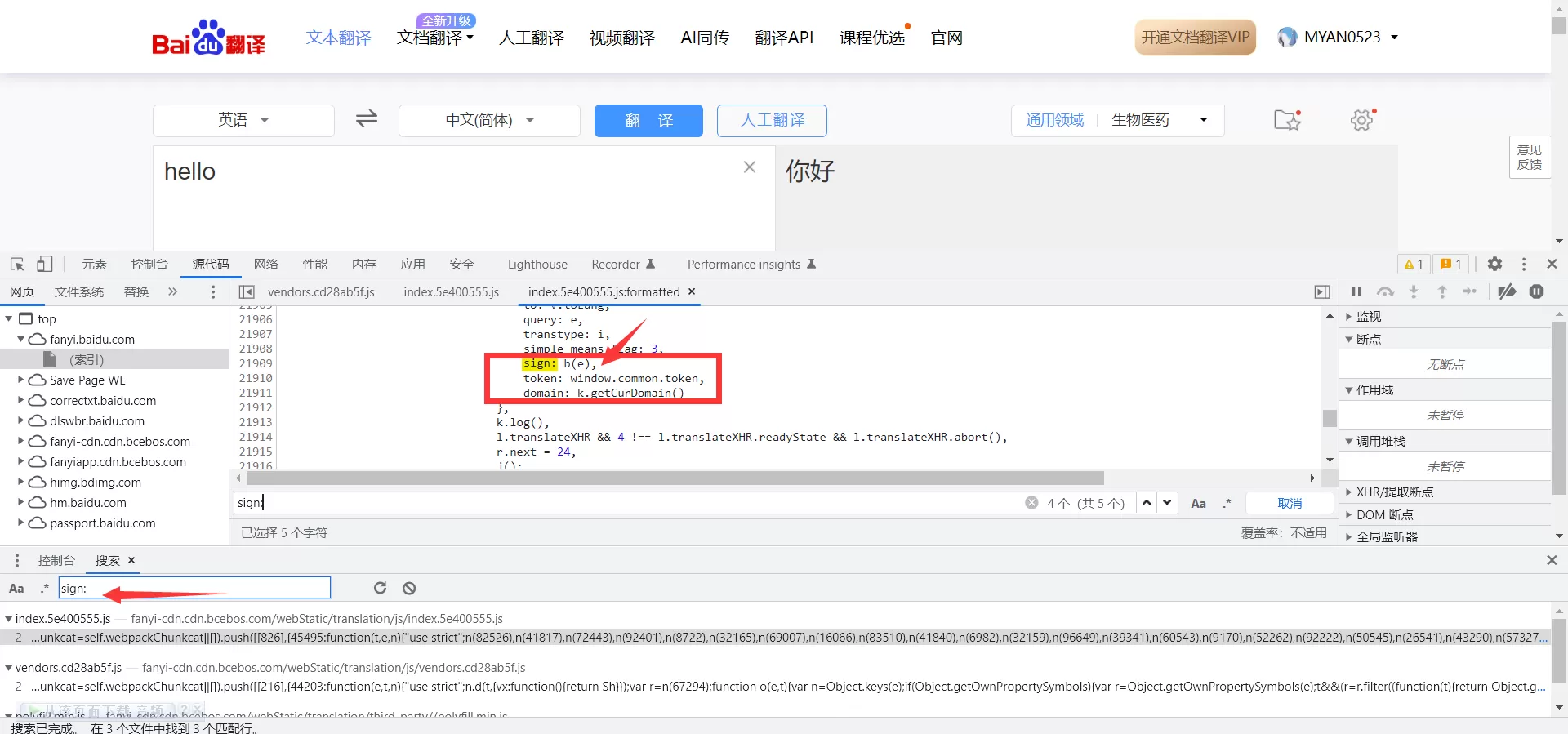
更换查询单词,发现token值并不变化,因此变化的只有sign值,接下来需要获取的sign的值;在JS文件中查询哪些文件中有sign这个变量,最后定位到如下图这个JS文件中,在该JS文件中,搜索sign,发现两处有可能生成sign值的地方,通过加断点调试,发现有一处是为了混淆视听无效代码;
进入生成sign值的函数中,如下图所示,发现代码及其繁琐,如果想要用python代码复现逻辑,需要耗费大量时间;因此尝试使用JS逆向的思想,在python中使用模块execjs运行JS代码,只要能够获得sign值即可;生成sign值的函数的参数,通过加断点调试,发现是输入的查询翻译的单词;
复制生成sign值的函数,为了防止该函数可能还会调用其他函数,可以将该函数附近的函数一并复制;以下是我复制的JS代码:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59function e(t, e) {
(null == e || e > t.length) && (e = t.length);
for (var n = 0, r = new Array(e); n < e; n++)
r[n] = t[n];
return r
}
function n(t, e) {
for (var n = 0; n < e.length - 2; n += 3) {
var r = e.charAt(n + 2);
r = "a" <= r ? r.charCodeAt(0) - 87 : Number(r),
r = "+" === e.charAt(n + 1) ? t >>> r : t << r,
t = "+" === e.charAt(n) ? t + r & 4294967295 : t ^ r
}
return t
}
var r = null;
// 源代码这里是t.exports = function(t),为了方便我调用该函数,做了修改
function l(t) {
var o, i = t.match(/[\uD800-\uDBFF][\uDC00-\uDFFF]/g);
if (null === i) {
var a = t.length;
a > 30 && (t = "".concat(t.substr(0, 10)).concat(t.substr(Math.floor(a / 2) - 5, 10)).concat(t.substr(-10, 10)))
} else {
for (var s = t.split(/[\uD800-\uDBFF][\uDC00-\uDFFF]/), c = 0, u = s.length, l = []; c < u; c++)
"" !== s[c] && l.push.apply(l, function(t) {
if (Array.isArray(t))
return e(t)
}(o = s[c].split("")) || function(t) {
if ("undefined" != typeof Symbol && null != t[Symbol.iterator] || null != t["@@iterator"])
return Array.from(t)
}(o) || function(t, n) {
if (t) {
if ("string" == typeof t)
return e(t, n);
var r = Object.prototype.toString.call(t).slice(8, -1);
return "Object" === r && t.constructor && (r = t.constructor.name),
"Map" === r || "Set" === r ? Array.from(t) : "Arguments" === r || /^(?:Ui|I)nt(?:8|16|32)(?:Clamped)?Array$/.test(r) ? e(t, n) : void 0
}
}(o) || function() {
throw new TypeError("Invalid attempt to spread non-iterable instance.\nIn order to be iterable, non-array objects must have a [Symbol.iterator]() method.")
}()),
c !== u - 1 && l.push(i[c]);
var p = l.length;
p > 30 && (t = l.slice(0, 10).join("") + l.slice(Math.floor(p / 2) - 5, Math.floor(p / 2) + 5).join("") + l.slice(-10).join(""))
}
for (var d = "".concat(String.fromCharCode(103)).concat(String.fromCharCode(116)).concat(String.fromCharCode(107)), h = (null !== r ? r : (r = window[d] || "") || "").split("."), f = Number(h[0]) || 0, m = Number(h[1]) || 0, g = [], y = 0, v = 0; v < t.length; v++) {
var _ = t.charCodeAt(v);
_ < 128 ? g[y++] = _ : (_ < 2048 ? g[y++] = _ >> 6 | 192 : (55296 == (64512 & _) && v + 1 < t.length && 56320 == (64512 & t.charCodeAt(v + 1)) ? (_ = 65536 + ((1023 & _) << 10) + (1023 & t.charCodeAt(++v)),
g[y++] = _ >> 18 | 240,
g[y++] = _ >> 12 & 63 | 128) : g[y++] = _ >> 12 | 224,
g[y++] = _ >> 6 & 63 | 128),
g[y++] = 63 & _ | 128)
}
for (var b = f, w = "".concat(String.fromCharCode(43)).concat(String.fromCharCode(45)).concat(String.fromCharCode(97)) + "".concat(String.fromCharCode(94)).concat(String.fromCharCode(43)).concat(String.fromCharCode(54)), k = "".concat(String.fromCharCode(43)).concat(String.fromCharCode(45)).concat(String.fromCharCode(51)) + "".concat(String.fromCharCode(94)).concat(String.fromCharCode(43)).concat(String.fromCharCode(98)) + "".concat(String.fromCharCode(43)).concat(String.fromCharCode(45)).concat(String.fromCharCode(102)), x = 0; x < g.length; x++)
b = n(b += g[x], w);
return b = n(b, k),
(b ^= m) < 0 && (b = 2147483648 + (2147483647 & b)),
"".concat((b %= 1e6).toString(), ".").concat(b ^ f)
}本文将上述JS代码保存为info.js,新建python文件,运行以下代码:
1
2
3
4
5
6
7
8
9import execjs
with open('info.js', 'r') as f:
jscode = f.read()
# 创建执行对象 并执行js代码
jsobj=execjs.compile(jscode)
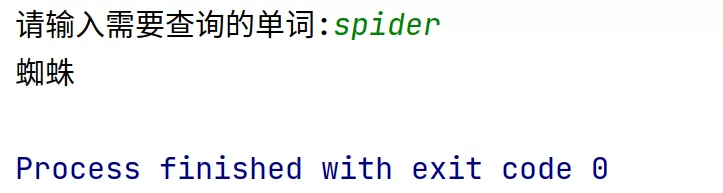
sign=jsobj.eval('l("hello")')
print(sign)运行完,提示找不到widow,在info.js中查找参数widow,查找到的代码如下:
1
h = (null !== r ? r : (r = window[d] || "") || "").split("."), f = Number(h[0]) || 0, m = Number(h[1]) || 0, g = [], y = 0, v = 0; v < t.length; v++)
这里widow有一个参数d,查找参数d的定义,代码如下:
1
var d = "".concat(String.fromCharCode(103)).concat(String.fromCharCode(116)).concat(String.fromCharCode(107))
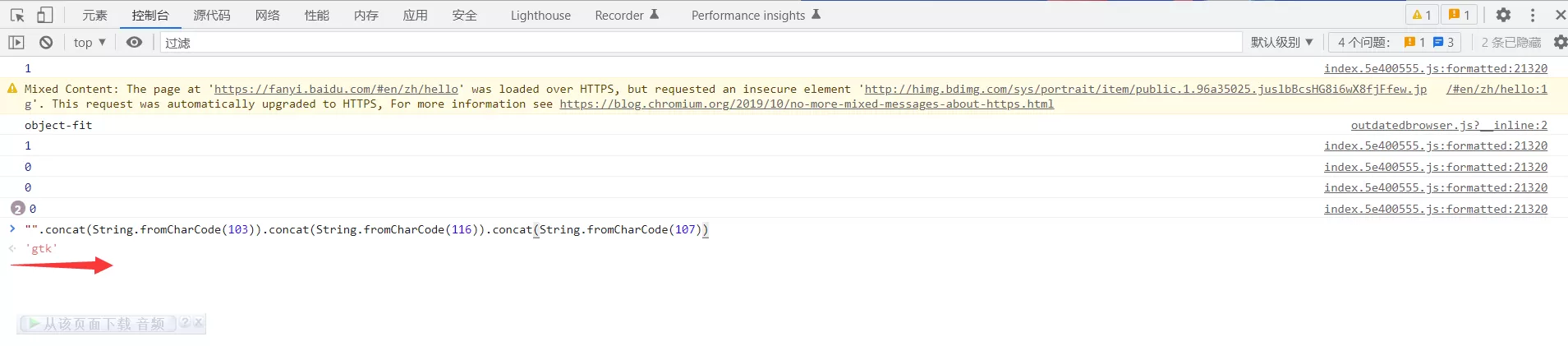
初步判断这个变量d是一个字符串,在控制台输入变量d的定义,得到字符串gtk:
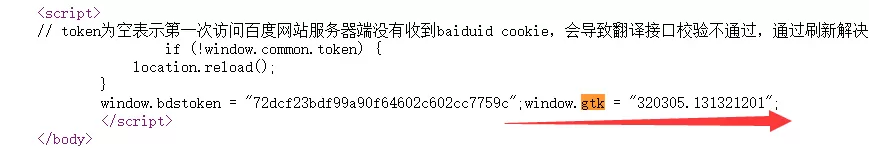
由于是widow,因此判断gtk应当是在网页源代码中,右键查看网页源代码,搜索参数gtk,得到参数gtk的值,更换其他搜索单词,发现该参数gtk的值并不变化:
得到gtk值后,将JS文件中window[d]直接替换成在网页源代码中搜索到的值,再运行python文件,运行成功,至此破解sign值到此结束
1
2
3x h = (null !== r ? r : (r = window[d] || "") || "").split("."), f = Number(h[0]) || 0, m = Number(h[1]) || 0, g = [], y = 0, v = 0; v < t.length; v++)
// 调换成
x h = (null !== r ? r : (r = '320305.131321201' || "") || "").split("."), f = Number(h[0]) || 0, m = Number(h[1]) || 0, g = [], y = 0, v = 0; v < t.length; v++)
整合请求数据
需要请求的参数分别是headers,请求地址,表单数据;其中headers直接复制即可,请求地址也是直接复制即可,表单数据中,变化的部分有sign值以及查询的单词;
代码演示
python文件:
1 | ''' |
JS文件
1 | function e(t, e) { |